In the intricate landscape of digital connectivity, advanced cybersecurity strategies are essential to safeguard against the ever-evolving spectrum of cyber threats. This article delves into the nuances of the top 10 cybersecurity threats, providing sophisticated insights into the methodologies employed by adversaries. Furthermore, it presents advanced strategies to fortify digital defenses and ensure robust protection in an era where cyber threats have reached unprecedented sophistication.
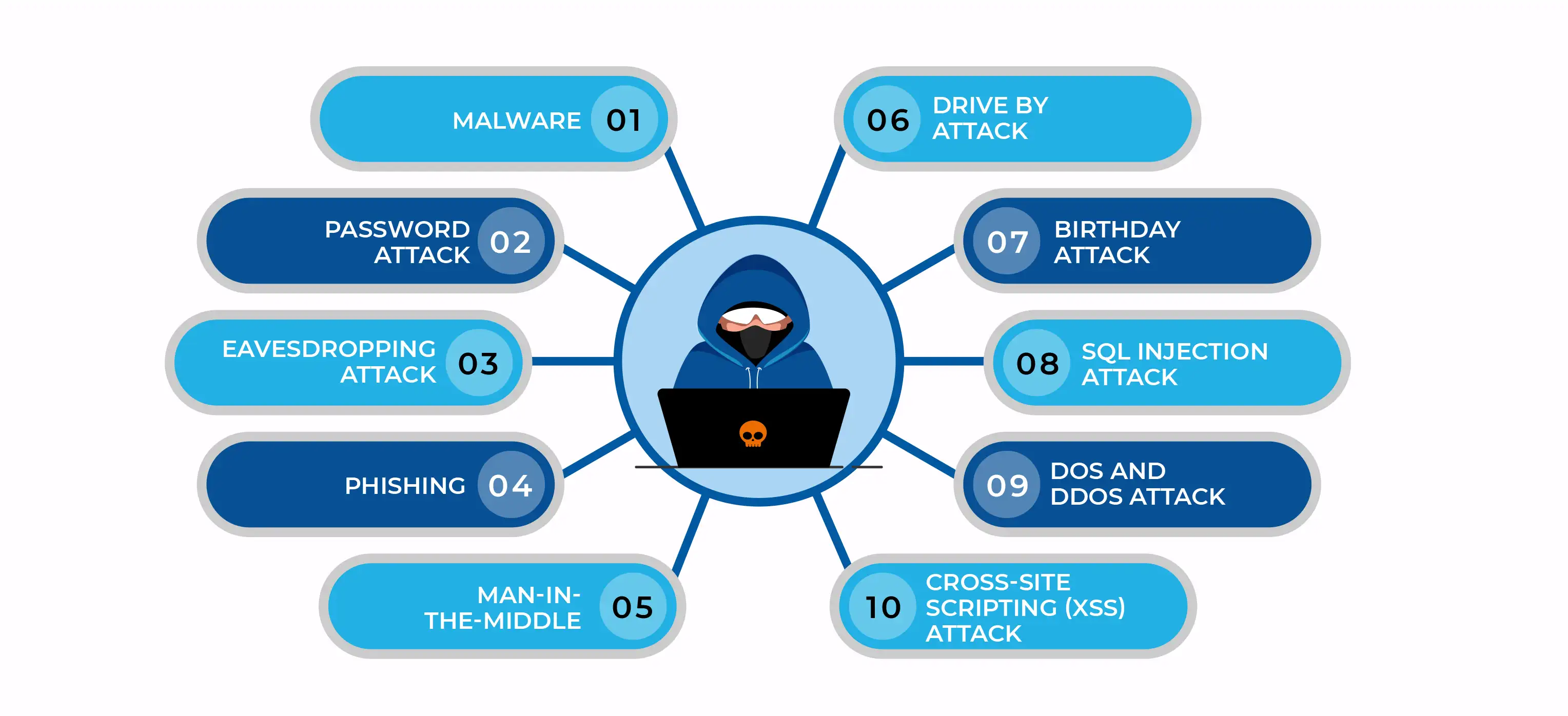
Top 10 Cybersecurity Threats: A Comprehensive Exploration
-
Advanced Phishing Techniques - Beyond the Surface:
- Examine sophisticated phishing techniques, including spear-phishing and whaling attacks. Explore how threat actors meticulously tailor their approaches to target high-profile individuals and organizations.
-
Polymorphic Malware and Ransomware - Adapting to Defenses:
- Uncover the intricacies of polymorphic malware and ransomware variants capable of dynamically altering their code to evade traditional security measures. Explore advanced countermeasures against these adaptive threats.
-
Advanced Social Engineering Tactics - Manipulating the Human Element:
- Delve into advanced social engineering tactics, such as pretexting and influence operations, that exploit psychological vulnerabilities. Explore defensive strategies that go beyond basic awareness to mitigate sophisticated manipulation attempts.
-
Zero-Day Exploits - Navigating Uncharted Vulnerabilities:
- Understand the landscape of zero-day exploits, which target undiscovered vulnerabilities in software. Explore advanced threat intelligence practices and proactive measures to detect and mitigate potential zero-day threats.
-
Password Cracking and Credential Stuffing - Breaking Digital Fortresses:
- Explore advanced techniques used by cybercriminals for password cracking and credential stuffing attacks. Analyze modern authentication mechanisms and adaptive authentication solutions to thwart sophisticated attacks.
-
Wireless Eavesdropping and Man-in-the-Middle Attacks - Securing the Airwaves:
- Examine advanced wireless attacks, including eavesdropping and man-in-the-middle attacks. Explore advanced encryption protocols and network monitoring techniques to secure wireless communication channels.
-
Fileless Malware and Memory Attacks - Exploiting Stealth Techniques:
- Uncover the stealthy nature of fileless malware and memory-based attacks. Explore advanced endpoint detection and response (EDR) solutions and memory protection mechanisms to combat these elusive threats.
-
Distributed Denial of Service (DDoS) Amplification - Orchestrating Large-Scale Attacks:
- Explore advanced DDoS techniques, including amplification attacks and botnet orchestration. Analyze sophisticated traffic filtering and mitigation strategies to ensure uninterrupted service during large-scale attacks.
-
Advanced Persistent Threats (APTs) - Sustained and Targeted Intrusions:
- Understand the intricacies of APTs, which involve persistent and stealthy attacks targeting specific entities. Explore advanced threat hunting and incident response practices to detect and mitigate prolonged cyber intrusions.
-
Cryptocurrency Exploitation - The Dark Side of Decentralization:
- Examine how threat actors exploit cryptocurrencies for illicit activities, including ransom payments and money laundering. Explore advanced blockchain analysis techniques and regulatory measures to curb cryptocurrency-related threats.
Advanced Cybersecurity Measures: Fortifying Digital Fortresses
-
Machine Learning and Artificial Intelligence (AI) in Cybersecurity - Predictive Defense:
- Explore the integration of machine learning and AI for predictive threat detection and automated response. Analyze advanced anomaly detection and behavior-based analysis for proactive cybersecurity.
-
Deception Technologies - Misleading Adversaries:
- Investigate the use of deception technologies to mislead and divert attackers. Explore honeypots, decoys, and misinformation strategies to create a complex and challenging environment for adversaries.
-
Threat Hunting - Proactive Cybersecurity Operations:
- Delve into the realm of threat hunting, where cybersecurity professionals actively search for indicators of compromise within an organization's network. Explore advanced threat intelligence integration and proactive hunting techniques.
-
Endpoint Detection and Response (EDR) - Real-Time Threat Management:
- Analyze advanced EDR solutions that provide real-time monitoring and response capabilities. Explore threat containment, investigation, and remediation techniques at the endpoint level.
-
Cloud Security Best Practices - Securing Dynamic Environments:
- Explore advanced cloud security strategies, including identity and access management, encryption, and continuous monitoring. Analyze the intricacies of securing dynamic and multi-cloud environments.
-
Behavioral Analytics - Identifying Anomalies:
- Understand how behavioral analytics can identify anomalous patterns and activities indicative of potential threats. Explore user and entity behavior analytics (UEBA) for advanced threat detection.
-
Incident Response Automation - Streamlining Responses:
- Examine incident response automation tools and orchestration platforms. Explore the integration of automated playbooks and response workflows to enhance the efficiency of incident response teams.
-
Secure DevOps (DevSecOps) - Integrating Security Into Development:
- Explore the principles of DevSecOps, where security is seamlessly integrated into the software development life cycle. Analyze secure coding practices, automated security testing, and continuous integration/continuous deployment (CI/CD) security.
-
Zero Trust Architecture - Reimagining Network Security:
- Understand the philosophy of zero trust architecture, where trust is never assumed, and every user and device is treated as untrusted. Explore micro-segmentation, least privilege access, and continuous authentication in zero trust environments.
-
Blockchain in Cybersecurity - Decentralized Trust:
- Investigate the potential applications of blockchain in enhancing cybersecurity. Explore the use of blockchain for secure identity management, decentralized authentication, and secure data storage.


ask me your doubts????
You must be logged in to post a comment.